Recently in Dec2021, a vulnerability was found in Log4j, an open-source logging library commonly used by apps and services across the internet. This vulnerability has shaken the entire world. To mitigate this vulnerability in Oracle Fusion Middleware, Oracle recommends to apply following patches .
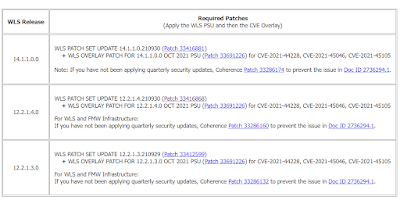
Download following patches for WLS Release 12.2.1.4
1. Download latest Opatch for WLS 28186730
2. For the WLS and FMW Infrastructure, if you have not been applying quarterly security updates, Coherence Patch 33286160 is a prerequisite.
3. WLS PATCH SET UPDATE 12.2.1.4.210930 (Patch 33416868)
4. WLS OVERLAY PATCH FOR 12.2.1.4.0 OCT 2021 PSU (Patch 33671996) for CVE-2021-44228,CVE-2021-45046
I will be applying these patches in windows environment.
SET ORACLE_HOME=D:\app\oracle\product\12.2.1.4
Set JAVA_HOME=D:\app\oracle\jdk
Apply patch 28186730 – This patch installs latest version of Opatch for FMW/WLS
D:\app\oracle\product\12.2.1.4\OPatch>%java_home%\bin\java -jar C:\Users\Administrator\Downloads\6880880\opatch_generic.jar -silent oracle_home=D:\app\oracle\product\12.2.1.4
Launcher log file is C:\Users\Administrator\AppData\Local\Temp\1\OraInstall2021-12-19_05-06-36PM\launcher2021-12-19_05-06-36PM.log.
Extracting the installer . . . . Done
Checking if CPU speed is above 300 MHz. Actual 2400 Passed
Checking swap space: must be greater than 512 MB Passed
Checking if this platform requires a 64-bit JVM. Actual 64 Passed (64-bit not required)
Checking temp space: must be greater than 300 MB. Actual 272082 MB Passed
Preparing to launch the Oracle Universal Installer from C:\Users\Administrator\AppData\Local\Temp\1\OraInstall2021-12-19_05-06-36PM
Installation Summary
….
….
….
The install operation completed successfully.
Logs successfully copied to C:\Program Files\Oracle\Inventory\logs.
Shutdown entire application services(Nodemanager , Weblogic , FORMS, Reports, OHS etc)
Navigate to patch location and apply the patch
unzip p33286160_1221411_Generic.zip
List out the installed components to see the installed Coherence version
C:\Users\Administrator>%ORACLE_HOME%/OPatch/opatch.bat lsinventory -jdk %JAVA_HOME% -inactive
Oracle Interim Patch Installer version 13.9.4.2.1
Copyright (c) 2021, Oracle Corporation. All rights reserved.
Oracle Home : D:\app\oracle\product\12.2.1.4
Central Inventory : C:\Program Files\Oracle\Inventory
from :
OPatch version : 13.9.4.2.1
OUI version : 13.9.4.0.0
Log file location : D:\app\oracle\product\12.2.1.4\cfgtoollogs\opatch\opatch2021-12-19_16-18-03PM_1.log
OPatch detects the Middleware Home as “D:\app\oracle\product\12.2.1.4”
Lsinventory Output file location : D:\app\oracle\product\12.2.1.4\cfgtoollogs\opatch\lsinv\lsinventory2021-12-19_16-18-03PM.txt
——————————————————————————–
Local Machine Information::
Hostname: CSAPP2
ARU platform id: 233
ARU platform description:: Microsoft Windows Server 2003 (64-bit AMD)
There are no inactive patches installed in this Oracle Home.
——————————————————————————–
OPatch succeeded.
cd C:\Users\Administrator\Downloads
C:\Users\Administrator\Downloads>%ORACLE_HOME%/OPatch/opatch apply 1221411 -jdk %JAVA_HOME%
Oracle Interim Patch Installer version 13.9.4.2.1
Copyright (c) 2021, Oracle Corporation. All rights reserved.
Oracle Home : D:\app\oracle\product\12.2.1.4
Central Inventory : C:\Program Files\Oracle\Inventory
from :
OPatch version : 13.9.4.2.1
OUI version : 13.9.4.0.0
Log file location : D:\app\oracle\product\12.2.1.4\cfgtoollogs\opatch\opatch2021-12-19_16-22-18PM_1.log
OPatch detects the Middleware Home as “D:\app\oracle\product\12.2.1.4”
Verifying environment and performing prerequisite checks…
OPatch continues with these patches: 1221411
Do you want to proceed? [y|n]
y
User Responded with: Y
All checks passed.
Backing up files…
Applying interim patch ‘1221411’ to OH ‘D:\app\oracle\product\12.2.1.4’
Patching component oracle.coherence, 12.2.1.4.0…
Patch 1221411 successfully applied.
Log file location: D:\app\oracle\product\12.2.1.4\cfgtoollogs\opatch\opatch2021-12-19_16-22-18PM_1.log
OPatch succeeded.
Unzip patch 33416868
Apply patch
C:\Users\Administrator\Downloads>%ORACLE_HOME%/OPatch/opatch apply 33416868 -jdk %JAVA_HOME%
Unzip patch 33671996
Apply patch
cd C:\Users\Administrator\Downloads\33671996
%ORACLE_HOME%/OPatch/opatch apply
Mitigation Plan
If patching is not possible at this time, you may mitigate the Log4j vulnerabilities with the below steps.
This mitigation applies to Log4j v2 prior to 2.16.0, including 2.15.
1. Navigate to the location:
ORACLE_HOME/oracle_common/modules/thirdparty/
2. Run the below command for the installed Log4j version 2 files:
12.2.1.3.0: log4j-1.2.17.jar – This is expected to contain a version 2 file
12.2.1.4.0: log4j-2.11.1.jar
14.1.1.0.0: log4j-core-2.11.1.jar and log4j-api-2.11.0.jar
Unix:
zip -q -d log4j*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Windows:
Use a zip utility to extract the contents as a .zip, remove JndiLookup.class, and re-zip.
Reference:-Security Alert CVE-2021-44228 / CVE-2021-45046 Patch Availability Document for Oracle WebLogic Server & Fusion Middleware (Doc ID 2827793.1)


Leave a Reply